Ethical Hacking Tutorial
Ethical Hacking Tutorial
Ethical hacking is a process of intruding into a network to find out threats. It is a process to find out the attacker who is causing a damage or loss of data , financial loss or other major problems.
Let’s find out what is hacking ?Hacking is process by which an unknown authority is entering your system without permission for some negative purpose or to cause damage. Ethical hacking is also a same process in which hacker is entering into the system with the owner’s permission to find out the weakness of the computer.
How to Become Ethical Hacker?
1. Hacker Types
The terms “HACKER” refers to the person who takes sensitive information out without the consent of the user. There are “ETHICAL HACKER” also who generally works to protect the data.
People think that hacking is illegal but if done with the consent of the user it provides security and privacy also. Even we have several sorts of jobs available for hackers.
Categories of Ethical Hackers
- Black Hat Hacker
- White Hat Hacker
- Gray Hat Hacker
- Green Hat Hacker
- Script Kiddies
Black Hat Hacker:
They are those hackers whose main motto is to hack for financial gains and for a thrill. They create various types of malware which are used for accessing the crucial and vital information. They steal all kinds of information from the user and blackmail the users. Whatever these hackers do they do it illegally. They work outside the reach of the government and against them too. Their main intent is a violation of policy and hacking personal and sensitive data.
White Hat Hacker:
They are called Ethical Hacker. Their main intent is to protect the data and contribute toward making the society a safe place to live. They find out the sensitive information which can be accessed by the unethical hackers thereby resulting in the protection. They do the job as a security researcher, penetration tester and access the data with the consent of the person so to protect them from the next hacking.
Grey Hat Hacker:
They are the combination of both Black and White Hat Hacker. They do provide security but with some incentive. They also take out the information from the user without the consent which makes them illegal too. They simply want some money rather than asking a lot of amounts.
Green Hat Hacker:
They are the newbies in the hacking world. They want to become a fully blown hacker but they are at the beginning of the phase. In other words, they are the Wannabees hackers. They are very curious in terms of learning coding also which is required for hacking.
Script Kiddies:
They are also the amateur hackers of the online world. They don’t want to learn much coding skills required to do all sorts of hacking. They simply download the tools and codes written by hackers and use them to get the attention of their friends.
2. Famous Hacker
Brief introduction of some popular hackers
- Garay Mckinnon
- Jonatan James
- Michael Calce
- Roman Seleznev
Garay Mckinnon
He was the hacker who was accused of hacking 97 us military and NASA computers in order to get the proper evidence of some confidential information. He used his girlfriend’s aunt’s home to hack the entire network and posted a message on the websites which were owned by the military with the information “your security is crap”. The damage done by him leads to $800,000 damage. All of his charges were dropped in 2012 after standing a trial in the UK court.
Jonatan James
He was the hacker who hacked into NASA and Pentagon. He broke and stole the data and software which cost around $1.7 million. When he was found guilty he was just 16 years old and just because of that he got six months house arrest and banned from the computers till he reached 18.
Michael Calce
He was also known by the name called mafiaboy. he started using computers when he was six years old. He once managed to shut down the yahoo for an hour and also launched a series of attacks eBay, CNN, Amazon. He was also a minor so he got custody of 12 months only.
Roman Seleznev
He is known by the name track2 and ncux. He is a Russian cybercriminal and did a lot of intrusions and intruded several institutions. He made money in billions and sentenced to 41 years in jail.
He is responsible for credit card dump operations.
3. Ethical Hacking Terminologies
Vulnerability:
A bug or glitch in the system which leads to the system getting compromised
Exploit:
A code that takes exploits the vulnerability of the software or the system.
Phishing:
It is a technique that is used to trick the user in order to get the crucial information out from the user that crucial information includes sensitive password, credit card information.
Encryption:
It is a process in which we will encode the message into human-readable data. Sometimes the data is encrypted to demand the ransom from the user.
Brute force attack:
This kinds of attack mean trial and error attack where software is used to guess the password.
Bot:
It is a software robot that runs some scripted code to read the content and information of the user.this can be used to get the sensitive data of the user.
DDoS attack:
They are done by the software or bots where several computers at a time will be sending the request to the website for accessing the website which will cause overloading of the system and thereby resulting in the crashing and shutting down of the servers.
SQL injection:
Using SQL to get sensitive information from the database is called SQL injection.
Spam:
This terminology means getting junk information like spam emails. This can also cause the introduction of malware into the system which resulted in the phrasing.
4. Ethical Hacking Tools
John the Ripper:
It is the password cracker tool used for breaking the password or for testing the strength of the password. for the encrytpion of the password, we used the password encryption algorithm and in order to break the password this tool first finds out the algorithm used and then decrypts the password accordingly.
Metasploit:
In order to test the software vulnerabilities, we need to use these tools which allow hackers or researchers to perform several kinds of attacks as it contains several frameworks.
Nmap:
This is called network mapper which is an open source tool used for the monitoring of the network and performs several functions like detecting port, network mapping and check for the vulnerability in the network.
Aircrack –ng :
This is a tool that provides features like cracking a password, brute force attack, access point attack, and network monitoring.
Burpsuite:
This is a tool used for security testing of web applications. This is used to do various things like scanning applications, checking vulnerability, technical reports, advanced crawling.
Acunetix:
These tools used for the purpose of scanning javascript, html5, and single page applications. It generates the compliance reports too.
Wireshark:
It is used for analyzing the traffic in the network.it is used for solving any issues which happened across the network. any kind of malicious activity, packet issues can be solved by the above tool. Any kind of intrusion is also detected by the analyzer tool.
Nikto:
It is also a scanner that is used to scan the vulnerability and web server scanner.it also do the server configuration checks.
5. Ethical Hacking – Skills
As responsible for the hacker it is your need to develop or upgrade the skills which internet skills, programming skills, good analytic problems resolving, etc.
- Very efficient programming knowledge for the expert hacker
- Networking knowledge for an expert hacker
- Database related knowledge for an expert hacker
- Prebuilt hacking tools become expert in hacking
6. Ethical Hacking – Process
The ethical hacking process is mainly divided into 5 types, it is not mandatory to follow a hacker in sequence but it is good.
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Clearing Tracks

7. Ethical Hacking – Reconnaissance
It is the first process involved in hacking to get sufficient information, This is also called as information collecting phase or footprint phase.we can collect the information from three groups.
They are
- Host
- Network
- People involved
This phase involved two types
Active:
Interacting directly to collect the data.
Passive:
Interacting in-directly to collect the data.
Scanning:
It is divided into three types
Port scanning: It will scan the particular port.
Network Map: Find the firewalls, routers, and topology, etc.
Vulnerability Scanning: Check the strength of the target.
Gaining Access:
It is used to enter into the target area to get more privilege to do whatever want.
Maintaining Access:
To maintain the connection in the background to monitor the system like Rootkits, Trojans.
Clearing Track:
To escape from the evidence all hackers will clear the tracking data.
8. Ethical Hacking – Sniffing
It is a process of capturing or monitoring the data packets which is passing the packets in the network. It will capture the data like account information, password, etc. It is in two types.
Active sniffing:
This sniffing we can do by using the switch on the LAN network.
Passive Sniffing:
This sniffing we can do by using the hub on the LAN network.
9. Ethical Hacking – FingerPrinting
It is used to identifying the present running os in the remote machine. It is also divided into two types they are passive and active
Active :
In this mode, special packets crafted types sent to the target machine and response is taken by the os.
Passive:
Remote host os finds by using the debugging packets captured by Wireshark.
10. Ethical Hacking Sniffing Tools
To performing the sniffing over a network many tools available and all the sniffing they have own features to support a hacker the information.
This Sniffing tool is a common application. Here we listed some sniffing
- BetterCAP
- Ettercap
- Wireshark
- Tcpdump
- WinDump
- OmniPeek
- Dsniff
- MSN Sniffer
BetterCAP:
BetterCAP is an incredible, adaptable and convenient instrument made to perform different sorts of MITM assaults against a system, control HTTP, HTTPS, and TCP traffic progressively, sniff for certifications, and significantly more., Wireshark. It is a standout amongst the most broadly known and utilized bundle sniffers.
Ettercap:
Ettercap is a moral hacking apparatus. It underpins dynamic and inactive analyzation incorporates highlights for system and host examination. Highlights, Ettercap is fit for sniffing an SSH association in full duplex
Wireshark:
Wireshark is a famous and amazing asset used to investigate the measure of bits and bytes that are moving through a system. This course will cover Wireshark from the eyes of a moral programmer. Wireshark in usually utilized by malware analyzers, blue groups, and other security protectors.
Tcpdump:
Moral Hacking – Sniffing Tools. Tcpdump. It is a notable order line bundle analyzer. It gives the capacity to block and watch TCP/IP and different parcels amid transmission over the system.
WinDump:
A Windows port of the well known Linux bundle sniffer tcpdump, which is a direct line apparatus that is ideal for showing header data.
OmniPeek:
OmniPeek is a business item that is the advancement of the item EtherPeek. Dsniff, A suite of tools intended to perform sniffing with various conventions with the goal of catching and uncovering passwords.
Dsniff:
Dsniff is an accumulation of tools for system reviewing and infiltration testing. dsniff, filesnarf, mailsnarf, msgsnarf, urlsnarf, and web spy inactively screen a system for intriguing information
MSN Sniffer:
Sniffing is the way toward observing and catching every one of the bundles going through a given system utilizing sniffing tools. It is a type of “tapping telephone wires” and become more acquainted with the discussion. It is additionally called wiretapping connected to the PC systems.
A potential programmer can utilize any of these sniffing tools to investigate traffic on a system and dismember data.
11. ARP Poisoning in Ethical Hacking
ARP has the abbreviation of the Address Resolution Protocol. It is utilized to change over IP addresses to physical locations on a switch. The host sends an ARP communicate on the system, and the beneficiary PC reacts with its physical location.
Count measures of ARP Poisoning
Static ARP entries :
These can be characterized in the nearby ARP store and the change arranged to overlook all auto ARP answer parcels. The impediment of this strategy is, it’s hard to keep up on enormous systems. IP/MAC address mapping must be disseminated to every one of the PCs on the system
ARP poisoning software detection :
these frameworks can be utilized to cross-check the MAC/IP address goals and affirm them in the event that they are confirmed. Uncertified MAC/IP address goals would then be able to be blocked.
Hacking Activity:
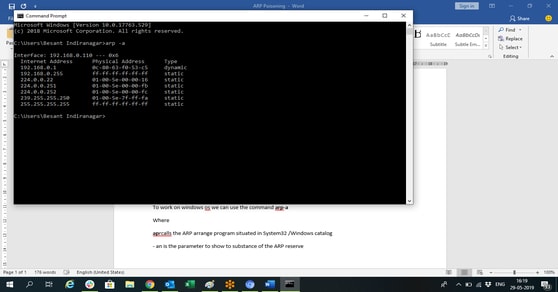
To work on windows os we can use the command arp-a
Where
parcels the ARP arrange program situated in System32 /Windows catalog. parameter to show to the substance of the ARP reserve
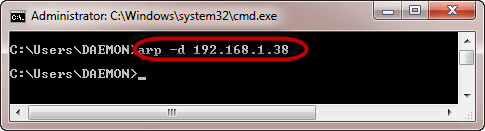
Deleting ARP:
To delete the entry we can use arp -d
12. DNS Poisoning in Ethical Hacking
DNS Poisoning is a procedure that fools a DNS server into trusting that it has gotten credible data when, as a general rule, it has not. It results in the substitution of false IP address at the DNS level where web locations are changed over into numeric IP addresses. It enables an aggressor to swap IP address sections for an objective site on a given DNS server with IP address of the server controls. An assailant can make counterfeit DNS sections for the server which may contain malignant substance with a similar name.
For example, a client types www.google.com, yet the client is sent to another misrepresentation site as opposed to being coordinated to Google’s servers. As we comprehend, DNS poisoning is utilized to divert the clients to phony pages which are overseen by the aggressors.
Example :
We should complete an activity on DNS poisoning utilizing a similar instrument, Ettercap.
DNS Poisoning is very like ARP Poisoning. To start DNS poisoning, you need to begin with ARP poisoning, which we have just talked about in the past part. We will utilize DNS parody module which is as of now there in Ettercap.
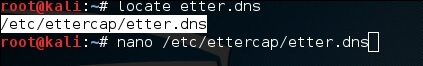
Steps 1: Open up the terminal and type nano etter.dns. This document contains all sections for DNS addresses which is utilized by Ettercap to determine the area name addresses. In this document, we will include a phony section of “Facebook”. On the off chance that somebody needs to open Facebook, he will be diverted to another site.
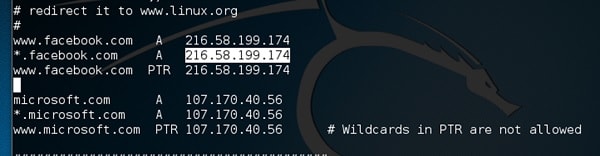
Step 2: Presently embed the passages under the words “Divert it to www.linux.org”. See the accompanying model.
Step 3: Presently spare this document and exit by sparing the record. Use Ctrl+X to file.
Step 4: After this, the entire procedure is same to begin ARP harming. In the wake of beginning ARP harming, click on Plugins in the menu bar and select dns_spoof module.

Step 5: After Activating

Step 6: It implies the client gets the Google page rather than facebook.com on their program.
Step 10: In this activity, we perceived how system traffic can be sniffed through various apparatuses and strategies. Here an organization needs a moral programmer to give arrange security to stop every one of these assaults. We should perceive what a moral programmer can do to avoid DNS Poisoning.
Defenses
As a moral programmer, your work could all around likely set you in a place of aversion instead of pen testing. What you know as an aggressor can enable you to anticipate the very procedures you utilize all things considered.
- Utilize an equipment exchanged system for the most touchy parts of your system with an end goal to detach traffic to a solitary fragment or impact area.
- Execute IP DHCP Snooping on changes to counteract ARP harming and mocking assaults.
- Execute arrangements to forestall indiscriminate mode on system connectors.
- Be cautious when conveying remote passages, realizing that all traffic on the remote system is liable to sniffing.
- Scramble your delicate traffic utilizing an encoding convention, for example, SSH or IPsec.
- Port security is utilized by switches that can be customized to permit just explicit MAC delivers to send and get information on each port.
- IPv6 has security advantages and choices that IPv4 does not have.
- Supplanting conventions, for example, FTP and Telnet with SSH is a compelling guard against sniffing. On the off chance that SSH is anything but a feasible arrangement, consider ensuring more established inheritance conventions with IPsec.
- Virtual Private Networks (VPNs) can give a powerful barrier against sniffing because of their encryption angle.
- SSL is an extraordinary safeguard alongside IPsec.
13. Exploitation in Ethical Hacking
Exploitation is a bit of modified programming or content which can enable programmers to assume responsibility for a framework, abusing its vulnerabilities. Programmers ordinarily use powerlessness scanners like OpenVAS, Nexpose , Nessus and so forth to discover these vulnerabilities.
Metasploit is an integral asset to find vulnerabilities in a framework.
In view of the vulnerabilities, we discover misuses. Here, we will talk about the absolute best weakness web search tools that you can utilize
Exploit Data Base:
https://www.exploit-db.com/ is the place where you can discover every one of the endeavors identified with a helplessness.

Common Exposures and Exposures:
(CVE) -Common Vulnerabilities and Exposures is the standard for data security helplessness names. CVE is a word reference of openly known data security vulnerabilities and exposures. It’s free for open use.

National Vulnerabilities Data Base:
National Vulnerability Database (NVD) is the U.S. government store of standards based defenselessness the board information. This information empowers computerization of weakness the board, security estimation, and consistency.
NVD incorporates databases of security agendas, security-related programming defects, misconfigurations, item names, and effect measurements.
By and large, you will see that there are two sorts of endeavors
Remote Exploits:
These are the sort of endeavors where you don’t approach a remote framework or system. Programmers utilize remote endeavors to access frameworks that are situated at remote spots.
Local Exploits:
Neighborhood adventures are commonly utilized by a framework client approaching a nearby framework, yet who needs to bridge his rights.
Quick Fix:
Vulnerabilities for the most part emerge because of missing updates, so it is prescribed that you update your framework all the time, for instance, when seven days.
Control Panel -System and Security- Windows Updates.

14. Enumeration
Enumeration means to get information from resources.In Information gathering Enumeration is one of the part.
In Ethical Hacking we are following a 5 step scenario. In that
- Reconnaissance (Information Gathering)
- Scanning
- Gaining Access
- Maintaining Access
- Clearing Tracks
Reconnaissance
Reconnaissance refers to the pre-attack phase where an attacker observes a
Target before launching an attack. It may include the target organizations
Clients, employees, operations, network, and systems
Information gathered in this phase
- Usernames, Group names
- Hostnames (pc)
- Network shares and services
- Service settings and Audit configurations
- SNMP and DNS Details
NetBIOS enumeration
NetBIOS stands for Network Basic Input Output System. It allows computers to communicate over a LAN to share files and devices like printers. NetBIOS names are used to identify network devices over TCP/IP.
SMB Enumeration
SMB stands for Server Message Block. It is mainly used for file share in both windows to Linux and Linux to windows.
Domain Name server / service / System
Domain name server
It consists of ZONEs
Forward lookup zone – Resolving HOST name to IP address
Reverse lookup zone- Resolving IP address to Hostname
IT consists of resource records (RR’s)
Domain name service — Runs on port 53
Works on both TCP and UDP
UDP — used for hostname and IP resolvation
TCP — Zone transfer
Domain name system
“/” (root server)
Top level domains (Zones) example: .com | .edu | .org | .mil | .gov | .net
Root servers maintain zone information (13)
Each root server is responsible for mainitining a zone’s information
Roots server can have information of more than one zone
Sublevel domain exmaples: .co.in | .co.uk | .in | .co.au | .info
DNS Resolution process for www.xyz.com
Client –> Client’s DNS server –> ISP’s DNS server
Server –> National ISP’s DNS server
Server –> .com Zone’s root server
Server–> xyz.com’s name server
Server–> Obtain www.xyx.com’s IP address
DNS Resolution process for mail.xyz.com
Client –> Client’s DNS server –> xyz.com’s name server
mail.xyx.com’s IP address –> Obtain
NTP Enumeration
NTP (Network Time Protocol) uses UDP port 123. NTP enumeration you can gather information such as a list of hosts connected to the server, IP addresses, system names, and operating systems running on the client system in a network.
SNMP Enumeration
Simple Network Management Protocol is AN application layer protocol that uses UDP protocol to take care of and manage routers, hubs, switches and different network devices. SNMP may be a widespread protocol found enabled on a range of in operation systems like Windows Server, UNIX servers similarly as network devices.snmp port 161
SMTP Enumeration
SMTP enumeration allows to find valid users on the SMTP server. Smtp nothing but simple mail transfer protocol and it’s port number 25..
Mail server configuration
Step 1: Prepare a PHP based mail and try openng it with browser
Step 2: Start Mercury mail server
Step 3: Go to Configuration > Protocols Modules and Select
- SMTP
- POP
- SMTP end-end
- SMTP relaying client
- POP debugging
- IMAP
Step 4: Restart Mercury and sort windowws to tiles
Step 5: Go to Configuration > Mercury Core module
Go to Local domains and set a domain name (Cycopslabs.com>
Step 5: Go to Configuration > Mercury SMTP and uncheck relaying
Step 6: Go to Configuration > MercuryE client and DNS records (8.8.8.8,1.1.1.1) (openDNS)
Step 7: Go to Configuration > Manage Local users and add user
Step 8: Restart Mercury
Step 9: Configure Outlook or Thunderbird
Name: Anything
Email address: user@localhost
Password: ******
Ignore warnings
15. Metasploit
System Hacking
System hacking is the process of trying to compromise the target system with the help of the information we collect from the pre-attack phases(Footprinting and scanning).
Metasploit
Metasploit is a Framework used to exploit particular vulnerability where we can find in vulnerability scan, and get access of the victim system.
- Exploits
- Payloads
Vulnerability: In simple words, vulnerability is a loophole, Limitation, or weakness that becomes a source for an attacker to enter into the system.
Exploit: It is a software tool designed to take advantage of a flaw(vulnerability) in a system for malicious purposes.
Payload: A payload is an action, or set of operations that has to be done on the target, once the exploit successfully launched. It can be any control or Denial of service, etc.
Metasploit usage
- Open Metasploit framework console in Kali Linux os
- Search exploit name/module
- Info exploit module path
- Use the exploit module path
- Show options
- Set RHOST (victim pc up)
- Set REPORT (victim port)
- Show payloads
- Set payload (payload module path)
- Show options
- Set LHOST (attacker up)
- Set LPORT (attacker port)
- Exploit
- Get cmd access of victim system
16. Trojan Attacks
They are the kind of the malware which comes into users computer without giving information to the users. This can be achieved by making user click on certain malicious links which leads to the downloading this malware. Once they comes into users system they can create lot of problem into the system of the users which includes opening unwanted popups , deleting several files, extracting some crucial information and provides pathway for various kinds of viruses.
Reason of Getting Trojan:
- Clicking on file present on the internet.
- Downloading the malicious files from the internet.
- Opening an email attachments.
- Opening a USB directly without using any antivirus.
How to be Protectd from Trojan Attacks?
- Proper use of antivirus is required.
- Opening a file from internet which can harm our computer is strictly prohibited.
- The email attachment should be checked before opening.
- Use of USB should be done only after scanning with the proper antivirus.
- Proper use of firewall and DNS.
Anatomy of Hacking
Phase 1:
- Information gathering
- Open web reconniance
- WHO IS reconniance
- SNMP reconniance
- SMTP reconniance
- DNS reconniance
- LAN reconniance
- WLAN reconniance
- Phase 2: Scanning
- Port scanning
- Vulnerability scanning
Phase 3: Gaining Access
- Remote code execution (RCE)
- Client-Side Exploitation
- Priviliage Escalation
Phase 4: Maintaining Access
- Post exploitation
- Viru, Trojans, Keyloggers and Backdoors
Phase 5: Clearing Tracks
- N/A
- Debriefing / Reporting
In the maintaining access we are installing back doors in victim system for a long time maintaining access.
Network Vulnerability assessment and penetration testing
Vulnerability assessment
Assess the vulnerabilities that might exists in an Operating system, application, protocol, hardware.
List of vulnerabilities — 60000+ nessus
Penetration testing
- Creating a proof of concept oof vulnerability by exploiting it.
- User credentials
- Screenshot of File system
- Add user account to system
- Screenshot of Desktop
- Put a file in the vulnerable system
Malware
Is a malicious program that infects a system.
Types of Malware:
Virus : It’s a malicious program that infects a systems with user interaction. CHi virus, Newfolder, SMSS
Creeper – 1981
Brain – 1986 (Boot sector virus)
Worms: It’s a malicious program that infects a systems without user interaction by using vulnerabilities.
Morris – David Morris (1988)
CERT – Computer Emergency Response Team
Trojans – (RAT — Remote Administrating Tool) Its a malicious program that infects a systems with user interaction by pretending to be a good program.
- Netdevil
- Backoffice / Backorifice
- Beast
Key loggers – Its a malicious program that infects a systems with user interaction and steals user entered keys.
- SC Keylogger
- Tiny Keylogger
Backdoors – Its a malicious program that infects a systems with user interaction by opening an unknown port at victims system.
Ad/Spyware – Its a malicious program that infects a systems with user interaction and takes control of useers browser.
Ransomware – Its a malicious program that infects a systems with user interaction and encrypts users sensitive data.
Scareware – Improper information will be fed to user and lure him to install malicious program.
Rootkit – Its a malicious program that infects a systems with user interaction and encrypts users designed to provide continued privileged access to a computer while actively hiding its presence.
Bots – Bots are tools used to control Zoombies
17. TCP/IP Hijacking
TCP/IP Hijacking in another term called it as active sniffing basically in the network the attacker will gain access to the host and which logically it disconnecting from network. It will be achieved to avoid password based authentication while starting the session.

TCP/IP establishes the connection usually in the below mentioned way.
We have two different possibilities when we try to hijack this connection,
- We can easily find the sequence which can be predicted it is a number and increases by 1, but don’t have a change to exactly predict it.
- Also we would use Man-in-the-Middle attack is other option and to put it in a nutshell, it is also called as network sniffing. We use some tools called Ethercap or Wireshark for network sniffing.
Example:
Usually two devices participate in a connection and in that the attacker will be monitoring the data transmission between these over a network and through which discovers the IP address of two devices.
The moment he discovering the ip of any one of the user, by DoS attack the hacker will put the other users connection and communication will be resumed by spoofing the disconnected user’s IP
Shijack:
Shijack is One of the best tool for TCP/IP hijack which is developed in python language and can be downloaded from the portal − https://packetstormsecurity.com/sniffers/shijack.tgz
Given is a sample command for the shijack
| Ec2-user:/home/ec-user/hijack# ./shijack eth0 10.0.0.100 53517 10.0.0.200 23 |
18. Password Hacking
- Hacking passwords are not very easy unless we have a vulnerable user. Finding a password using all possible combinations will take years. Password hacking will be easily done using keyloggers or while accessing spoofed website.
- Most common way of compromising the password is
- Using Most common passwords. (ex. Name, phone number, etc..)
- Sharing passwords with others (ex. sharing with friends.)
- Writing down the passwords (ex. writing pin numbers in ATM Card, writing password in note book, etc.)
- saving the passwords in browsers.
- There are lot of tools available to hack passwords.
- We can use keyloggers which can monitor and capture all the keystrokes and sent it to the person who planned this event.
- We can run a loop of entering passwords in all possible combinations to find it.
- We can host a spoofed website and sharing it, if a person login to the website using their credentials we can easily find it. (just like hosting a spoofed website of Facebook or google and finding the password).

19. Wireless Hacking
- Hacking wireless network completely depends on ” Device we use in network”, ” Device Configuration ” etc.
- Wireless access points are mostly open to all which gives an opportunity for all the people to try connecting even if you are not aware of passwords. (trying with incorrect passwords)
- Performing a vulnerability assessment and exploit the discovered vulnerabilities to gain access to network.
- Setting complex password for wireless access point with alphanumerical and special characters
- Changing wireless access point password on regular interval
It is very important to change the router login password during initial setup (under http://192.168.1.1)from default password

20. Social Engineering
Social Engineering is a technique. There are multiple ways to do this. The ultimate aim of the hacker is to get the user sensitive information. Using that data the hacker will pretend like original user and will get more or sometimes unlimited access of the organization or system.
For example, human social engineering includes getting sensitive information like account number, phone number, name, address from the old document or carbon copy paper.
Computer social engineering is mostly done by phishing technique. I will give a practical example of phishing attack which will be helpful you to understand completely.
Phishing is a technique, hacker will create a copy of an application which is very similar to a original application. Hacker will send a invite to the targeted user in any way.
If the user is not aware of the attack, the user will visit the application created by hacker and will give any sensitive data asked in the hacker's application. Because as per user it is original application which he/she can believe. Once the required data is obtained, the application will redirect the user to original application page.
So the user mostly won'taware of attack. I use Gmail application for demonstrating phishing attack. I have created a webpage which is very similar to Gmail signin webpage. Please click here to try.
Hacker will send a mobile message like the user's gmail account is at risk and need his attention. Hacker will provide this link https://bit.ly/2F8FDMs in the message. User is unaware of this attack and will visit this link. He/she will provide the information asked in the webpage, after obtaining the data the webpage will redirect the user to original gmail page. So the user will not be aware of attack.
Techniques to avoid it
To avoid human social engineering, the users should have a knowledge about social engineering and should not disclose his sensitive data to anyone.
Properly dispose any old document or carbon copy paper from the company.
To avoid computer social engineering please check whether the application invite is from correct source, check site information before giving any data in it.
21. DDOS Attacks
Distributed Denial of Service or DDOS attack is a technique used to make targeted website unavailable for other users. A hacker will not have access to the target website but if the hacker wants to bring down the service of website he/she will use DDOS attack.
This is a legitimate way of attack, so the server can't avoid it easily. In detail, consider a website can normally serve upto 255 connection. So the website will be available for first 255 users, if the 256th tries to access the website then the server will not be able to serve for the request. Now the website is serving for 255 users or connections, consider these 255 connections are done by hacker, then the website service is down for other users until hacker stops sending request to the website.
Since it is a legitimate access to website but by flooded access from single host, the hacker denying the service of the website to other users. It is called as Denial of Service.
But in normal scenario a website can serve to huge number of connections. Thus, a single system will not be enough to attack websites. So the hacker will first hack the enough systems required to attack a website using RAT(Remote Administration Tool) virus.
This virus will give access of desktop or laptop he/she hacked. Now using all these hacked system hacker will execute an command to make connection with website from each hacked system.
Consider a hacker hacked 1000 desktops and laptops. Consider each system can make 255 connections to the target website, thus because of hackers command 1000 * 255 = 255000 connections are made to the target website. Because of this huge flood of connection, server will be busy in serving to those connections, thus the website will be unavailable for general user or access to the website is denied. Since the Denial of service is done using distributed system or host, this techniques is called as Distributed Denial of Service(DDOS).
Mostly DDOS attack is done using Botnet. Botnet is a script which contains RAT virus script. This script has ability to get the instruction from hacker from remote location and execute the command in hacked host. Also this Botnet is a virus which will have the ability to move from one host to another. Thus this botnet will spread to any number of systems in no time.
There are many other techniques to do this. You can try it yourself by using following technique without any external software. This technique is called as ping of death. Create and save a .bat file by entering this following
script :loop
ping <target website ip> -l 65500 -w 1 -n 1
goto :loop
After saving the file, right click on it and Open. Now a loop of ping request is send to the target website with packet size more than 65536 bytes. Because of big packet size, the TCP/IP fragmentation in website will break the packet and send it to server. Due to constant ping request and fragmentation process, the server will crash. Thus the service is denied.
22. Cross Site Scripting
Cross Site Scripting is a attacking technique which can be done if the application has vulnerability. It is mostly done through client side using HTML, Javascript. From the name cross site scripting you can understand this technique is injecting our scripting on another'site(cross site).
Hacker will inspect the target site and find flaw in the code. The f law will allow the general user of the site to enter data(like input field in form), in non vulnerable site these user entered data will be treated as string but the vulnerable site will process user entered data.
For example, javascript is a coding language used in website's client side which is very powerful and capable of getting almost any client information like session data, sending server request and receiving server response and display it or even send it to anyone.
I will give a practical demonstration for easy understanding. But to understand this attack you need have knowledge of attacking language. In my demonstration attacking language is javascript. so you need basic knowledge how the javascript works.
I created a webpage which is vulnerable to Cross site scripting. Please click here to visit the webpage. After visiting give any random data to login, after login button is clicked a session will be created by the server and stored in a cookie.
A cookie can survive to anytime based on the server side coding. I created this site with session cookie can live upto one day. Now your session and cookie are created. In this case the hacker will send a link to the targeted user which will performs cross site scripting based on the vulnerability. Here the vulnerability is, there is a parameter in the url which will get the user data and process like an instruction in the javascript.
Mostly the probability of occurrence of this scenario is very less. Once you enter test site, it will give a alert with your session id(If logged in).
Hacker will send link like
http://www.tnkschools.com/CEH/css/css.php?param=alert(%27Hacked Session Value : %27%2B%0D%0AgetCookie(%22sessionid%22)) ,
by click this link your session id will be retrieved by the script and will be processed as per hacker's instruction. In above scenario, using the link I am performing a cross site scripting to get session id using a javascript user defined function 'getCookie(%22sessionid%22)' to get session cookie and displaying it using alert command, you can send it to any one also.
Technique to avoid it
If there is any place to get user input like input field or url parameter, it should be sanitized before processing. Sanitizing includes adding escape sequence to input or limiting the input length, etc.
23. SQL Injection
SQL Injection is one of the most dangerous technique and vulnerability of all. This technique is also done only if the application is vulnerable and uses users input data for attack. Unlike cross site scripting this vulnerability will allow the hackers to manipulate the SQL command which will allow the hackers to illegal access of site database data.
For example, there is a site with SQL Injection vulnerability, the hacker will attack the website's admin page and gets the admin access. Thus hacker will get access to all data of site.
I will demonstrate this attack. To understand this attack you need to have basic knowledge of SQL coding. I have created a webpage with sql injection here . The SQL command works based on condition clause knows WHERE. Usually sites are designed in the manner to get username and password of as input from users and using that data they will perform SQL operation to check whether there is any matching record in database using WHERE clause.
If WHERE clause returns TRUE value then matching record for username and password is found, the server will create a session for user and grant particular access to user. If not, the server will display as incorrect password.
Hacker will send a data to the server using vulnerability(input field or url parameter)which will send data to server. Because of vulnerability the server will run the SQL command with attacker's data which will manipulate the SQL command to return record even if the username and password is incorrect. Thus, the hacker will get access based on the script.
I created the test site with 2 input field where you can give username as admin and password as admin for login. If any data is incorrect the site will returns incorrect username or password alert. Following is the SQL command widely used for password and username checking
SELECT * FROM table_name WHERE (username = '(user input username)') and (password = '(user input password)')
Instead of admin in username and password field I am giving 1' or '1' = '1 . By this input the SQL command will becomes
SELECT * FROM table_name WHERE (username = '1' or '1' = '1') and (password = '1' or '1' = '1')
Now you can see as per the condition username = '1' the WHERE clause return FALSE but as per '1'='1' it always returns TRUE, same for password. Thus the commandnreturns all records. As per script, if the SQL command returns record then the backend script will grant access to the user.
Technique to avoid it
It is same as cross site scripting, if there is any place to get user input like input field or url parameter, it should be sanitized before processing. Sanitizing includes adding escape sequence to input or limiting the input length, etc.
24. Pen Testing
Pen Testing or Penetration Testing is a procedure of testing followed by many organizations to reduce the security flaws in the system. Since it is a theory topic, there is no demonstration and will be similar to the tutorial link you sent.
Usually, pen testing is done by certified persons. They will perform various testing in various scenarios as per procedures.
Since pen testing is done on production system or development system, the environment will be unavailable for general use during this process. So there should be proper planning. Also the pen tester will attack the system in all aspect, so there should be proper signing before the process start.
Professional Ethical Hackers or pen tester use open source tools or automated tools to perform testing on a field on a particular time. If the tester found any security breach, then he/she will report the organization about the security hole.
Types of penetration Testing
A pen tester will perform testing based on various scenarios. For example, in one scenario the tester will have no data access to system, in another case the user will get partial access to the system. They are differentiated using following type
Black Box
In this method, pen tester will not have any data about organization. Thus the attacker will act like public user.
Gray Box
In this method, pen tester will have partial data about organization like domain name server.
White Box
In this method, pen tester will have all data about organization like domain name. network, etc.
External Penetration Testing
In this method, pen tester will be in outside of the organization and will tries to attack server, webpage, public DNS server, etc.
Internal Penetration Testing
In this method, pen tester will be in inside the organization and tries to attack system.
Penetration Testing is costly, so usually organizations performs it annually or if any new application or new infrastructure is added or if any major update or security patch applied to the system.


 +1 201-949-7520
+1 201-949-7520 +91-9707 240 250
+91-9707 240 250