
What is Ethical Hacking?
What is Ethical Hacking?
Ethical Hacking is also known as Penetration Testing. This is a performance of penetrating into networks or system to search for the vulnerabilities, and threats from a system which can be easily attacked by a malicious attacker and lead to financial loss, data loss, or various other chief reparations.
Nowadays, computers are very obligatory to run a fruitful business. It is not possible to have a secluded computer system and for sure, all the computers are required to be interacted to enable communication with peripheral dealings. While networking and integrations are performed, systems are exposed to the outside world and thus results in hacking.
As per the survey conducted by Cyber Security organizations, it is clearly known just because of illegal hackers, Indian companies have lost about $4 billion in the year 2013.
I hope you all are aware that hacking is unlawful and such actions can end up in dangerous penalties if caught. Many people are sentenced to imprisonment just because of hacking. To progress the system or network security, Ethical Hacking takes place for setting the susceptibilities hunted at the time of testing.
There are few tools and approaches used by malicious hackers and similar processes are used by the Ethical hackers too but with the authorization of the sanctioned person to enhance the security system and protect the systems from various malicious users. A few examples of ethical hacking are penetrating networks, creating procedures to crack passwords, or dislocating network services.
Below are the chief points to take care of Ethical Hacking:
- Written permissions to examine the network and try to modify the security settings
- Esteem the individual or business’s privacy
- Gain faith of the customers by guaranteeing the security of data and security
Why Ethical Hacking?
Now we have a question “why to use Ethical Hacking? So, let us see the reasons for using the Ethical Hacking.
Preparation for a cyberattack: It is very simple for the cyberattacks can abolish an occupation, particularly when coming to a small-sized business. There are many companies that are not well prepared for cyberattacks.
Ethical hackers are good at finding the threat operation and understand the process of using new information and procedures to attack the business. Security specialists working with ethical hackers can easily prepare and handle future attacks. This process is useful in reacting to the continuously altering nature of operational threats.
Hunting the Susceptibilities: To determine the effectiveness of security measures, update the security system, identify the vulnerabilities, Ethical Hacking is necessary. Once the ethical hackers complete the evaluation part in an organization, a report is sent to the company heads regarding the vulnerable areas.
For example, uncertain applications, password encryption under insufficient state, and unprotected systems that are running with unpatched software. Based on this report and data, organizations can perform a few tests to make ends up in a few decisions on how and where to progress their security attitude to avoid cyberattacks.
Cybercriminals are using different demonstrating approaches. These demonstrations provide various techniques of hacking handled by executives used to attack their systems and cause chaos with businesses.
Introduction of Ethical Hacking
Ethical hacking is a process of intruding into a network to find out threats. It is a process to find out the attacker who is causing damage or loss of data, financial loss or other major problems.
Let’s find out what is hacking? Hacking is processed by which an unknown authority is entering your system without permission for some negative purpose or to cause damage. Ethical hacking is also the same process in which hacker is entering into the system with the owner’s permission to find out the weakness of the computer.
Ethical hackers are also called white hat hackers or white hat. Ethical hackers are like agents who secure there owner’s information. This process had started in the early 1980s. Then only the USA government had started in there defense systems to protect from unknown threats but in the 90s the internet became the most popular amongst the business community to publish adds and for e-commerce and other news etc.
The community easily understands the threat of loss of personal information about there own, client and employees.
In the year 1993 two computer security analyzers, Dan Farmer and Wietse Venema publish a report on how to get control of such an attack. They had published a report on the internet about how to prevent hacking by using the same tools and techniques.
But their procedure was very much time consuming and complicated, so they made a software gathering all the needed tools and techniques and named it SATAN(Security Analysing Tool for Auditing Network). The SATAN tool had the capability to detect the loopholes and guide the user to overcome the problems.
The two words- Ethics and Hacking, don’t seem to go hand in hand. After all, hackers are considered as people who lurk behind a computer screen and commit illegal acts. Therefore, when heard for the first time, Ethical hackers can be thought of as fish from the same pool. But it could not be further from the truth. In reality, Ethical Hacking refers to detecting the weak spots and vulnerabilities in terms of security of a computer system or a network by imitating the actions of a hacker.
The term “Ethical Hacking” was coined by IBM Vice-President John Patrick in 1995[2], but the concept of Ethical Hacking had been around since much earlier. Ethical hacking is also known as Penetration testing, intrusion testing, or red teaming.
You might have heard about someone’s online accounts being ‘hacked’ by a third party. This mostly happens in the context of stealing personal details from a system, for example, bank account details, credit card details, emails, and other personal information that a person stores for online transactions. Hacking of such information can cause considerable inconvenience for the person whose details have been compromised.
The term ‘hacking’ is used to describe the process of finding points of access in a computer system with the goal to copy or use the information stored in it. Typically, hacking is done to get unauthorized access with the intention of stealing personal information. However, Ethical Hacking is a completely different process in which a computer system is checked for weaknesses and testing. This type of hacking is not associated with stealing or misuse of stored information, and thus, is not illegal.
In other words, Ethical Hacking involves intrusion in a computer network to identify its vulnerability and potential points where the system could be attacked or compromised. Ethical hackers may use the same methods as criminal hackers to gain access to a computer network or system, but they do so with permission and authorization.
Techniques of Ethical Hacking
There are few ethical hacking techniques that are generally used by hackers to attack businesses and enterprises. Few are discussed below:
- To find vulnerabilities, we need to scan ports. Few port scanning tools like Nessus, Nmap or Wireshark are helpful for Ethical hackers to scan an organization system, recognize the entire open ports, get to know the vulnerabilities available on each port and take corrective steps and act accordingly.
- Analyzing patch installation procedures is the next technique used by the Ethical Hackers. This is to ensure that we don’t introduce any new susceptibilities in the updated software that can be oppressed.
- Accomplish Sniffing and networking traffic examination using suitable tools is one of the best techniques.
Ethical Hackers
Specific computer specialists are frequently appointed in most of the companies to find the weak points and vulnerabilities and fix them. People who can hack into the system with complete permission are known as ethical hackers. Same skills, similar methods, and techniques are used by all the Ethical Hackers for analysis and avoid organization.
Ethical hackers use their skills and many of the same methods and techniques to test and sidestep the company’s IT security which is said to be immoral counterparts. Ethical hackers are used to documenting the found out key points and afford suggestions on how to overcome those security issues in order to strengthen the overall organization security.
The companies whose networks are connected to the Internet or delivers an online service must always target the penetration testing which is effective handles and performed by Ethical Hackers.
Based on the intention of the hacking process, we have three (3) types of hackers, White Hat Hacker, Black Hat Hacker, and Grey Hat Hacker. As the name clearly defines, white hat hackers are used for good purposes, whereas black hat hackers are meant for wrong activities.
White Hat Hackers
Hackers who are working for any good purpose with complete proper access and permissions are called White Hat Hackers. Their intention is not to damage a system, but they ensure to hunt for the computer’s weaknesses and perform penetration testing and vulnerability analysis. Ethical hacking is one of the top demanding jobs available in the software industry and White Hat Hackers is completely legal.
Plentiful companies are hiring ethical hackers to have a wonderful security system. White Hat hackers are sure to hold a UG or PG degree in Computer Science or IT. For a better scope and best job, certification on hacking is an advantage.
Black Hat Hackers
A black-hat hacker is an illegal actor who enters into the system or network without any legal permission. A black box ethical hacker is the one who does not know anything about the organization on which they perform the attack.
These hackers simply try to impose harm by conceding error-filled website functions, unsecured security systems or closing systems.
This process is very for stealing or gaining access to the most important financial data, passwords, and a few other crucial personal data. The astonishing fact of this type of hackers is they frequently utilize a set of common hacking activities.
Grey Hat Hackers
A Grey Hat Hackers is a combination of black box hacking and white box hacking. We cannot expect any intention for this kind of hacking, but their attacking activities are for fun purposes. Just like that, they try to adventure security within various networks or computer systems without possessor’s knowledge or permission.
Their only intention is to acquire the attention of the system owners and be praised for the so-called wonderful hacking work. Grey Hat hackers will not run behind the data or money or information while hacking, neither they work for a good purpose. We can see more Grey Hat Hackers all over the world when compared to the other two hacker types.
Apart from the above mentioned three (3) major Hackers, there are few other hacker types too which are Red Hat, Blue Hat, Green Hat, and Script Kiddie.
Hacking tools used in common
Hackers are using a variety of tools to achieve a faultless hack and they are listed below:
Keyloggers
Keyloggers is an expressly intended tool used to record or log each key pressed on a computer. The documented file is later saved, which contains website details, usernames, accessed applications, and snapshots. You can retrieve the personal messages, credit card numbers, passwords, contact numbers, passwords, and a few other data that are typed on the system.
Rootkits
There are few hackers who take the remote access of a computer system interacting with the internet and that’s where rootkit software tool takes place. The original use of a rootkit is to open a system’s backdoor to resolve a few software problems. Inappropriately, hackers are now using this program to threaten an operating system from its users.
To install the tool rootkits in a target’s computer, Phishing attacks, and social engineering are the most important methods. On successful installation completion, hackers can access and govern the system in a secret manner. This process provides them a chance to steal vital data or shut down the system.
Vulnerability Scanner
To categorize and perceive various system weaknesses available in communication systems, networks, networks, etc, a vulnerability scanner is used. Ethical Hackers are utilizing this most common procedure to find all the probable ambiguities and fix those issues instantly.
Different Phases of Ethical Hacking
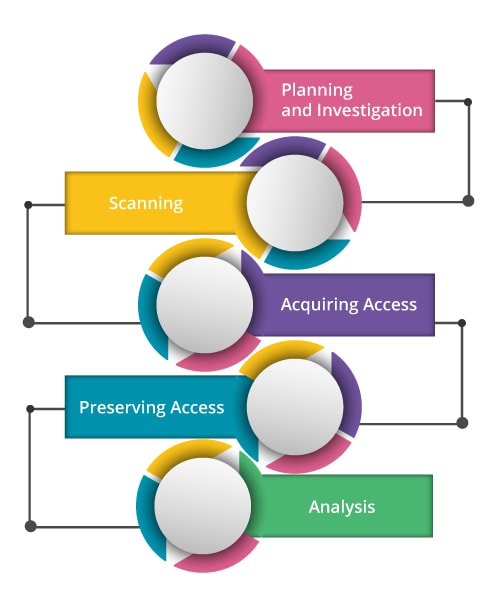
While performing penetration testing, we need to perform proper steps and they are discussed below:
Step:1
Planning and Investigation: The initial step for Ethical Hacking is to describe the possibility and mission of a test along with the testing methods which are mandatory to be performed. This step will also discourse the aptitude to comprehend the budding vulnerabilities and the way that target works. With the help of foot-printing tools, the potential foot-printing is done through various email, web services, search engines, web services, social network sites, network, DNS, etc.
Step: 2
Scanning: Next to the planning and investigation phase, we do have a scanning process. This step is to recognize the numerous intrusion efforts performed by the target in two methods. Scanning is done when the application code is operative and the other one is when the application code is motionless. The most practical method to appreciate the performance of an application in real-time is scanning at the time of functioning.
Step 3
Acquiring Access: Gaining Access is the step where the web application is criticized with the help of backdoors, SQL injections, and cross-site scripting. Through this phase, it is easy to retrieve the vulnerabilities and later data can be stolen, stop the traffic, and affect the rights to realize the damage volume that can arise.
Step 4
Preserving Access: To steal the entire valuable data and financial information, this step wakes up. The vulnerability is utilized as a determined presence in the infested system for an extended duration. You can also spread vulnerability within the network by maintaining access for a longer time.
Step 5
Analysis: On completing the penetration test, result compilation happens. This result is finalized by analyzing and remarking the vulnerabilities broken, data access, and the duration that a tester can stay unobserved in the system.
Process of Ethical Hacking
There is a step by step process to get the proper result in Ethical hacking.
Planning:
The authority has to make a full-proof plan for a successful project. They have to implement critical ideas to build the project more secure to access.
Reconnaissance:
This is a process of gathering information about the attack as much as possible and to take the needed steps to neutralize it. It could be any step like phone tapping, searching past employee records, etc.
Enumeration:
It is a process in which all the collected data are gathered to make appropriate strategies to fight against bug or theft
Vulnerability Analysis:
Vulnerability analysis is a process in which all the gathered information is used in a practical to compare with a known vulnerability. Information can be gathered from anywhere if it is suitable for detecting loopholes of the system .Internet is the most powerful source of information.
Exploitation:
After all, this process exploitation is the most important process in which all gathered information and planning are used as a tool to defend the attack. Sometimes it gets the expected results. Sometimes the system reacts unexpectedly due to the impact of the whole process.
Final analysis:
The final analysis is the phase in which the program conductor check all the vulnerability are fixed and to categorize the threat and ensure a secure environment.
Deliverables:
This is the process of meeting results. Some deliverables are brief like how to fix attacks; others are vast like the source of the attack, types of attack, how they are found, how to defend from those attacks and which tools are used, in a descriptive way.
Integration:
Finally, it is very important to ensure that no such threat can harm the system if it happened there would be proper tools or methods to detect and prevent the threat.
Ethical hackers have to ensure some claws, like when entering the targeted system have to inform the authority, only enter in the affected file but don’t interfere any other sources, bound by the local or the company laws, always keep record of work done, do not peek in others privacy, do not use any other tools except yours, last and most important thing is always inform about your findings cause the authority will take necessary steps for prevention.
How to Become Ethical Hacker?
An Ethical Hacker is a person who uses his knowledge of hacking and putting it into use for discovering security risks in a system, instead of exploiting that security flaw for his own benefit. Ethical hackers are also referred to as Whitehat Hackers or simply as Whitehats. Ethical hacking has always been a part of system security, ever since the early days of the internet.
The best part of Ethical Hacking is that whitehats get paid for their efforts. Many tech companies like Apple and Google have bounty programs under which they offer rewards to Ethical hackers for discovering flaws in their systems. Ethical hacking has become a full-fledged career at present with multiple educational institutions and universities offering courses on Ethical Hacking.
Certifications on Ethical Hacking
Below are the certifications available for Ethical Hacking concepts:
| S. No | Category | Certification Name | About Certification |
| 1. | Core | Certified Network Defender (CND) | The major focus of CND certification is about creating network admins that are well qualified in detecting, shielding, and retorting to the network threats. You can get hands-on experience on all the chief tools of network security and methods. Through this certification, you will get a strong knowledge of network security operations and technologies. The exam duration is approximately 4 hours and the number of questions is 100. |
| 2. | Certified Ethical Hacker (CEH) | CEH is the world’s top unconventional certification containing the most used 20 security domains that are used in the current days to enhance the organization’s information security position. The exam duration is 4 hours and 125 questions are posted in the exam. | |
| 3. | Certified Ethical Hacker (CEH- Practical) | In this certification exam, you will need to demonstrate the application of Ethical Hacking methods like Detection of Operation System, networking scanning, vulnerability analysis, identification on threat vector, web app & system hacking and so on. The duration of this exam would be around 6 hours. | |
| 4. | Certified Ethical Hacker (CEH- Master) | The world’s top performance-based ethical hacking certification is CEH – Master, which is well verified and available through online courses as well. On completing this certification, you will be able to say “Yes, I am clear, I can work all alone”. Once you clear the CEH Master and CEH Practical certifications, you will get the award from EC-Council. | |
| 5. | Advanced Level | Certified Threat Intelligence Analyst (CITA) | The development of the CTIA program was a collaboration with threat intelligence and cybersecurity experts all over the world to aid various companies to recognize and moderate business hazards. All the mysterious internal and external threats can be converted to known threats. An organized method for constructing active threat intelligence is taught from this course. |
| 6. | EC-Council Certified Security Analyst (ECSA) | ECSA provides you a group of wide-ranging methodologies that encloses various pen-testing needs in different categories. The exam duration for this course would be around 4 hours and the number of questions is 150. You need to get 70% to pass this level of certification. | |
| 7. | EC-Council Certified Security Analyst (ECSA- Practical) | ECSA-Practical is to test an individual skill to accomplish exploit and threat research, teach to write own exploits, modify payloads, and make perilous choices at various pen-testing phases which can make or disrupt the entire valuation. | |
| 8. | Expert Level | Licensed Penetration Tester – Master (LPT) | If you are ready to become a master in pen-testing tools and methodologies, then you need to opt LPT program where you can face the firmest challenges in a scheduled environment. You can easily get knowledge on advanced ideas like pivoting between networks, scanning against defenses, deploying proxy chains, and how to use web shells. Live online, Self-study, In-person training, and Master class are the different training options available with the LPT course. |
Skills grabbed by Ethical Hackers
On completing the above mentioned Ethical Hacking certifications and leading your career as an Ethical Hacker, then you are expected to have proficiency in networking, database handling, and operating system. For better communication, excellent soft skills are also expected. The chief technical skillsets that an ethical hacker must have are DNS spoofing, SQL Injection, Session hijacking, and spoofing, handle numerous network attacks, password predicting and breaking, and network traffic sniffing. Apart from all these mentioned skills, a very common skill expected is creative thinking as they must face all the ingenious ways used by the black hat hackers. The fact is it’s a duty of ethical hackers to foresee and take preventive measures.
A Career in Ethical Hacking
If you have completed the Ethical Hacking certifications, you can try for various hacking roles like Security Analyst, Information Security Manager, Information Security Analyst, Security Consultant, Penetration Tester, and Certified Ethical Hacker. You can easily get a chance to work in the military and for secret intelligence agencies such as NSA, CIA, and Mossad. An average salary for an ethical hacker would approximately $90,000 yearly as per the report shared by PayScale in the year 2019. With a few years of experience, you can draw up to $120,000 per year and it keeps on increasing based on your experience.
Must Read: Cyber Security Frameworks
Why choose Ethical Hacking as Career
- There are a few top companies that offer very good pay for ethical hackers. Such companies are S.Air Force, S.Army, Booz, Hamilton, Allen, General Dynamics Information Technology Inc, etc.
- Individuals who are good at hacking can work in different sectors like hotels, financial institutions, airlines, etc.
- Ethical hacking is a perfect choice to make your entry to different domains.
- Pre-requisites to become an ethical hacker are not a big list, whereas only a bachelor’s degree in computer science is expected.
- Ethical Hacking is an ever-growing field as it protects various systems that contain all the valuable information.
- If you are a black hat hacker, it becomes very simple for you to turn out to be a white-hat hacker with all your hacking skills.
- If you are a Grey hat hacker, you can simply have fun without breaking the law.
- The job title “Ethical Hacker” is a cool title that you can casually and happily mention to other people when asked for your job role.
The other basic concepts need to concentrate are you need to think out of the box, do a few hands-on exercises to perform self-learning, and try to get more information. Use the crucial key called “internet” for all your queries and become a master in your Ethical Hacking career.
Ethical hacking can be used for the benefit of a party in a multitude of ways
- Ethical hacking can be used to determine what are the loopholes and flaws of a system. Furthermore, among the loopholes discovered, ethical hacking also helps in diagnosing which loopholes of the system design are actually security flaws that can be used by a malicious hacker to compromise the system.
- Ethical hackers employ different tools to discover the different ways a malicious hacker can possibly gain access to the system. Ethical hackers also attempt to discover the extent of access that can be acquired by a hacker once he/she starts exploiting these loopholes.
- There might be a plethora of security flaws that might be discovered when an ethical hacker examines a system. All these flaws are critically scrutinized and the security flaw which must be fixed first is determined.
At first glance, it might seem that adopting ethical hacking as a career choice is a perfect choice. However, it does come with its downsides.
- Ethical hacking is a controversial subject because of the ‘Ethics’ part. Ethical views differ from person to person. Hence, there is always a risk of people with wrong end goals may be acting as ethical hackers. As one’s personal motives cannot be known by others, ethical hackers have always been questionable. Although certain certifications are available for ethical hackers, like CEH, that doesn’t guarantee whether or not an ethical hacker will always remain liable for his actions.
- Ethical hacking courses have been added to certain curricula in different educational institutions. However, this doesn’t guarantee whether or not a student shall use his knowledge of hacking responsibly. Furthermore, it can be debated that white hats can operate without the knowledge of the owners of the system. Although they might have the best intentions in mind, they may come across select information that the owner would like to disclose. Such situations always create conflicts of interest and lead to complicated scenarios.
- Every day, new web-based threats and codes are written for the sole purpose of fooling online security systems. Therefore, people involved in ethical hacking always have to be on top of their game. Ethical hackers have to get themselves recertified in order to keep them up-to-date with the latest threats that are plaguing our online world.
Ethical hacking treads a thin line in the sense that there is very little difference between illegal hacking and legal hacking. It requires the constant motivation to push oneself beyond the usual train of thought to detect security flaws that might be hiding deep inside a system. It is a constantly evolving field that protects us from unscrupulous hackers and making our increasingly online lives more secure.
How is Ethical Hacking Beneficial?
An ethical hacker understands the thought process of criminal hackers and knows the tools and techniques that they use to enter computer networks and systems. This means that ethical hacking is a great way to control cybercrimes, and is extremely useful in the following ways:
Identification of weaknesses and vulnerabilities of a computer system or network:
Ethical hackers are able to find out the potential threat points in any system or network and thus, help in fixing them and safeguarding against future attacks on the system by criminal hackers.
Assessments for the performance of networks:
Ethical hacking is an excellent way of analyzing and assessing the performance of upgraded networks.
Maintaining stringent national security:
Ethical hacking is an indispensable tool for protecting sensitive and important data of national importance from criminal hackers, anti-national elements, and terrorist groups.
Establishing secure networks:
By means of ethical hacking, it is possible to create trusted and secure networks that ensure a safe online transaction and activities.
Continuous quality assurance:
Ethical hacking and quality assurance go hand-in-hand, and ethical hackers can complete safety testing for different types of software.


 +1 201-949-7520
+1 201-949-7520 +91-9707 240 250
+91-9707 240 250